14) which of the following are breach prevention best practices
Breach prevention best practices for the prevention of. Cybercriminals target non-public personal information NPI.

How To Prevent Data Breaches In 2022 Upguard
247 help from Expert Tutors on 140 subjects.

. Ensure that your sensitive data is backed up regularly in case of a ransomware attack or system failure that causes loss of data. Remediation Accessed N PHI transmitted orally PHI on paper PHI transmitted electronically correct All of the above-----11 Which of the following are breach prevention best practices. Before you can prevent a data breach you need to know the sensitive data you collect store transmit or process.
Which of the following are breach prevention best practices. Established a national set of standards for the protection of PHI that is created received maintained or transmitted in electronic media by a HIPAA covered entity CE or business associate BA b. Other terms for this phenomenon include unintentional information disclosure data leak information leakage and also data spillincidents range from.
PCs cell phones PDAs and the network says Pappas. Which of the following are breach prevention best practices. Consider designating staff to carry out security monitoring.
All of the above answer a. All of the above You can help prevent a breach by accessing only the minimum amount of PHIPII necessary andby promptly retrieving documents containing PHIPII from the printer. Discuss best practices for preventing breaches.
Do you have strong password policy and is it being adhered to. Which of the following are breach prevention best practices. Remediation Accessed N PHI transmitted orally PHI on paper PHI transmitted electronically correct All of the above-----11 Which of the following are breach prevention best practices.
Breach prevention strategies TheftLoss. Access only the minimum amount of PHIpersonally identifiable information PII necessary. They need to be secure at the host eg.
Access only the minimum amount of PHIpersonally identifiable information PII necessary. Best Practices in Breach Prevention - Minimizing the Risk of a Breach. Out of the box AWS offers.
What are breach prevention best practices. Access to over 100 million course-specific study resources. Which of the following are breach prevention best practices.
Access only the minimum amount of PHIpersonally identifiable information PII necessary B. He recommends campuses have firewalls. Best Practices in Breach Prevention Develop appropriate security measures Monitor compliance with required measures Comply with reporting requirements W.
Addresses three types of safeguards - administrative technical and physical. Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or lock your workstation when it is unattended Promptly retrieve documents containing PHIPHI from the printer. Promptly retrieve documents.
You should always logoff or lock your workstation when it is unattended for any length of time. Remediation Accessed N PHI transmitted orally PHI on paper PHI transmitted electronically correct All of the above-----11 Which of the following are breach prevention best practices. Since cloud security is not widely understood it may be difficult to delineate it in the context of more general information security.
The focus of the linked case studies is ePHI although a HIPAA data breach can occur with paper records. S3 Breach Prevention. However these 30 best practices for preventing a data breach can reduce the risk and respond to an attack more effectively.
20 Which of the following are breach prevention best practices. Protect your most critical digital assets by segregating them and prioritizing them in your business continuity plan. A single technology cannot provide complete protection.
14 Which of the following are breach prevention best practices. Full access to over 1 million Textbook Solutions. Regular backups of your most sensitive data should be a part of this IRP to help you mitigate the damages a data breach could cause to business functions.
Unless When patient data or patient healthcare information is referenced in the case studies and best practices linked here it refers to ePHI. B- Logoff or lock your workstation when it is unattended. Promptly retrieve documents containing PHIPHI.
10 The HIPAA Security Rule applies to which of the following. One of the most common causes of a data breach is weak password policies. 10 The HIPAA Security Rule applies to which of the following.
A- Access only the minimum amount of PHIpersonally identifiable information PII necessary. Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or lock your workstation when it is unattended Promptly retrieve documents containing PHIPHI from the printer All of this above correct 3 The minimum necessary standard. Access only the minimum amount of PHIpersonally identifiable information PII necessary B.
Protects electronic PHI ePHI c. Promptly retrieve documents containing PHIPHI. Identity sensitive data collected stored transmitted or processes.
2 Which of the following are breach prevention best practices. Best Practices for Enterprise Cloud Security. Compliance required by 92314 New BAAs executedrenewed after 12513 Must conform to new rules.
Institute report suffering at leas t one data breach in the past 2 years Data breaches could be costing the healthcare industry upwards of 62 billion per year A breach of medical information costs healthcare organizations an average of 22 million per breach Interestingly the value of medical information on the black market has. 3 2015 Definitions. Logoff or lock your workstation when it is unattended.
Following this sheet is the Summary and Next Steps sheet a. Logoff or lock your workstation when it is unattended. When a data breach occurs involving a cloud service the impulsive reaction is to denounce using the cloud at least for sensitive information.
Access only the minimum amount of PHIpersonally identifiable information PII necessary. Logoff or lock your workstation when it is unattended C. Access only the minimum amount of PHIpersonally identifiable information PII necessary.
Covered entity is a health plan healthcare clearinghouse or healthcare provider who transmits. Password policies that include regular rotation and high levels of.

What Is Endpoint Security Definition Key Components And Best Practices Toolbox It Security

Top 4 Human Errors In Cyber Security How To Prevent Employee Mistakes Ekran System

Orca Security Launches Industry S First Cloud Risk Encyclopedia To Provide Ongoing Education For Cloud Security Best Practices Business Wire
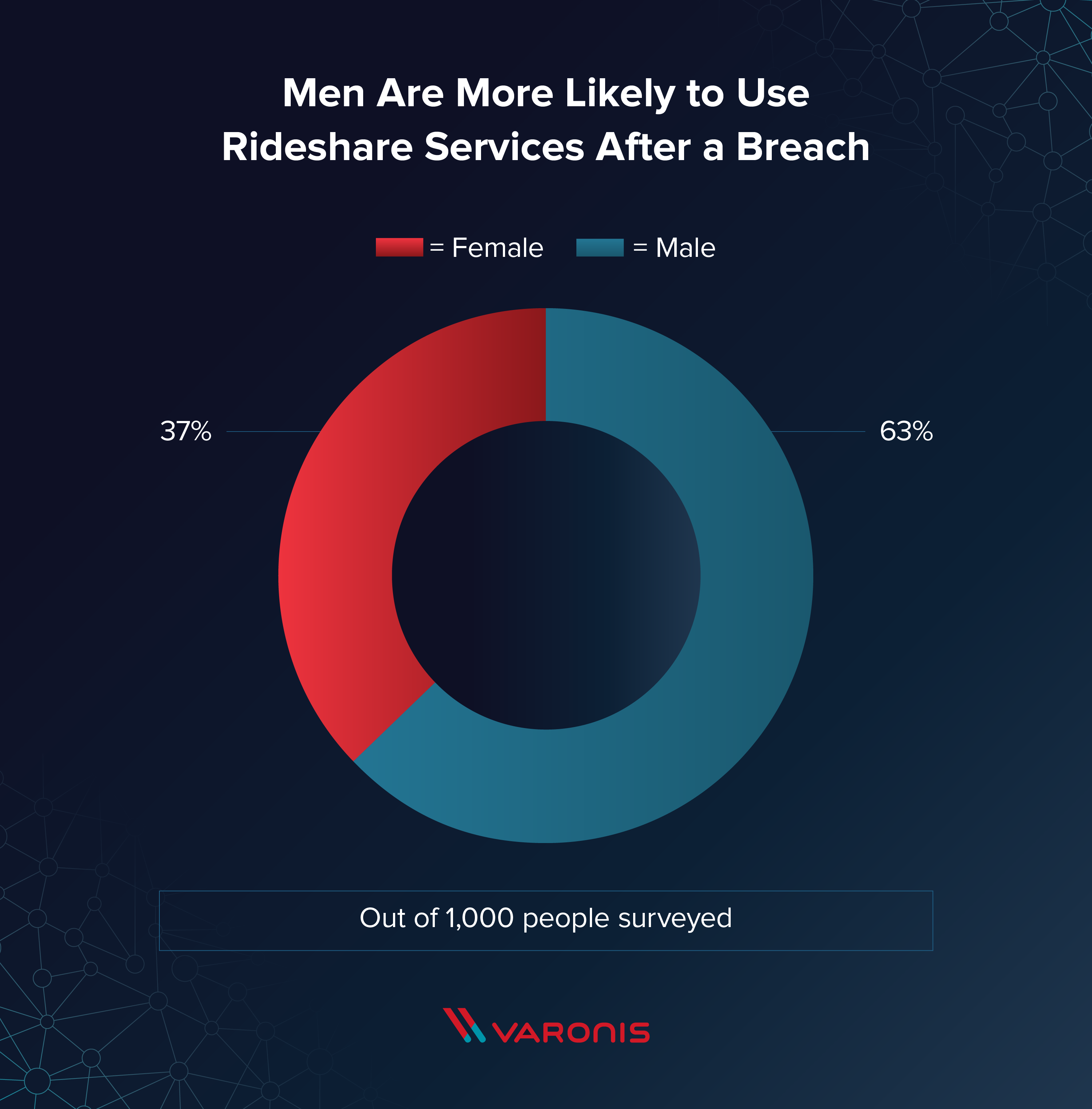
Analyzing Company Reputation After A Data Breach

Law Firm Cybersecurity Compliance Requirements To Follow Ekran System

Recent Cyber Attacks Data Breaches In 2021
5 Examples Of Security Breaches In 2018 Metacompliance

Top 16 Tips For Preventing Insider Data Theft Data Loss Prevention Currentware
6 Steps To Developing A Data Breach Response Plan Spectral

Analyzing Company Reputation After A Data Breach

What Is A Man In The Middle Attack Mitm Attack Prevention
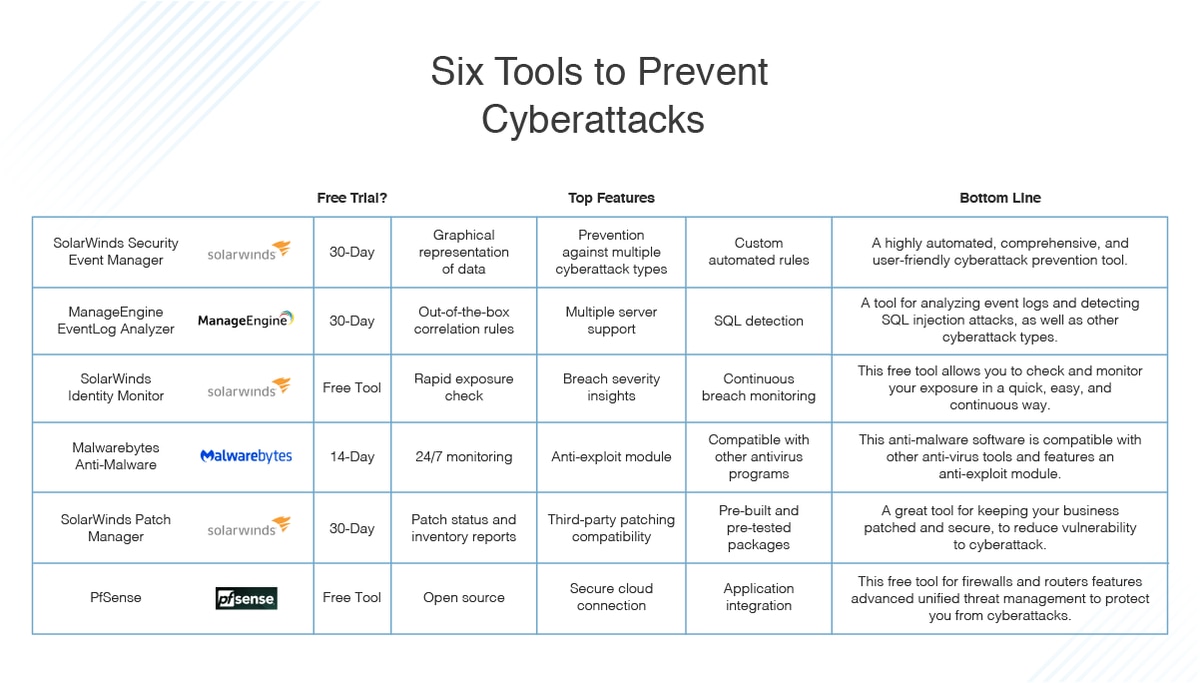
Top 6 Common Types Of Cyberattacks Dnsstuff
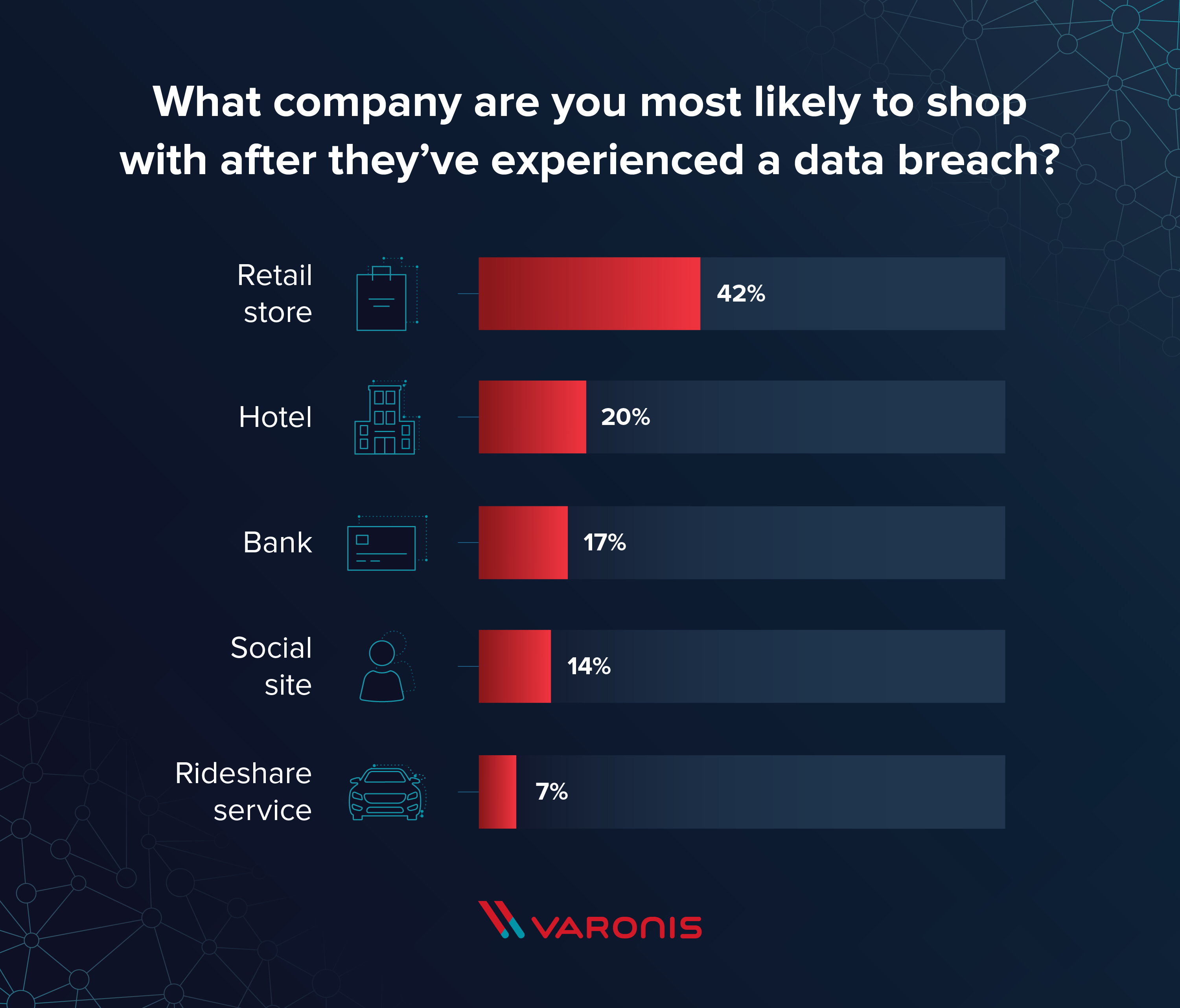
Analyzing Company Reputation After A Data Breach

Enterprise Data Breach Causes Challenges Prevention And Future Directions Cheng 2017 Wires Data Mining And Knowledge Discovery Wiley Online Library

Hipaa Pa Refresher Test Flashcards Quizlet

How To Prevent Data Breaches 12 Best Practices Paysimple


